Introduction
(This post has been sourced from a well known tutorial from Hackforums.net)
I have already written 2 posts on Denial of Service attack. The first one gives an insight to the working of Denial of service by bringing in practical examples (bus stop scenario and online multiplayer game scenario). The second one tells us about the various Denial of Service attack. I'm linking both the articles here for you to read if you want to-
I have already written 2 posts on Denial of Service attack. The first one gives an insight to the working of Denial of service by bringing in practical examples (bus stop scenario and online multiplayer game scenario). The second one tells us about the various Denial of Service attack. I'm linking both the articles here for you to read if you want to-
The thing is, while these two are pretty good reads (first one is a must read for everyone), I read something on HackForums.net which completely captured my attention. This tutorial was found in the premium tutorials section, and looked like this-
I asked coolmagicdude2 if I could post his tutorial on blog, as it would help a lot of users. He agreed. So this tutorial has not been written by me but a well known hacker from hack forums, who calls himself Druidtton of Darksunlight. I loved the tutorial and hope you'd enjoy it too. The tutorial is in first person and has many references to his personal experiences. I haven't replaced the first person to third (I to he, my to his). I have also removed all links, and replaced some.
Denial of Service attacks(or Distributed Denial of Service attacks[DDoS]) are a form of organized attacks with the goal of taking down a server by overloading it. Often by sending useless information(packets) to a server in massive amounts.
In-fact about a year ago I found one of my (his) websites was accidentally DoS-ing darksunlight.com(I use darksunlight as my webhost) because my PHP script made an infinite loop that sent the same information over and over and over into darksunlight's SQL databases. This one page took this EXTREMELY powerful server down twice in less than a minute. That site has since been deleted.
That story demonstrates that it does not take more than a simple "error" in your code to overload a server.
Keep in mind that altough spreading knowledge is my main goal, performing DDoS attacks is indeed a federal crime in the US.
It is also an international offence and will be punished according to the local laws of the individual's country.
But enough talk. I will now show you a quick example of a DoS attack of sorts you can do on your local computer.
We will take down YOUR computer.
Step 1
Open up notepad, mousepad, or your favored equivalent.
Step 2
Type in this simple batch command
Code:
:a
start
goto a
Step 3
Save as "dossample.bat" making sure you select "All files" from the "File Type" dialog.
Step 4
Run that sucker, but save your work first, as this will crash even the best computers in a matter of minutes.
An infinite loop has been created that has filled the RAM with useless and massive amounts of CMDs(or Terminals for you Unix folk)
DDoS attacks work much the same way, except instead of replicating an infinite number of CMDs, they send information(packets) to the server over and over and over again until the server crashes.
Next we will be discussing the simplest form of DDoS.
Please note that I will be pinging my Localhost. You should too.
Perhaps one of the simplest ways to DoS is by using the 'ping' command built into most operating systems, including all windows and Linux distributions.
Step 1
Start up your server. Mine is apache, but that is beside the point, the server type does not matter. If it has an IP address, it can be pinged. (He paced up really unexpectedly here. You might want to skip this part if you haven't created any local server using apache or any other program.)
Step 2
Type in the ping command
Code:
ping -t -a -l 65500 localhost
Step 3
Press enter and watch it ping the localhost over and over until[/b]
your server crashes, or you get tired of waiting for it to crash.
Since most modern servers can take the stress of the ping flood, you will need to get all your friends to help you ping to bring your server down. Or even slow it down.
-t - It will continue to ping the server until the command is closed, or stopped.
-a - Resolves the adress to host names.
-l - Size.
By default the ping will send 32bytes of data to the server, so you must change this to a bigger number. The maximum is 65,500bytes, so that is what we used.
If you send a server any number higher than 65,500bytes it will instantly crash. This is called "Ping of Death".
Like any other thing with the suffix "of Death" it is very rare, and hard to accomplish indeed.
In order to learn more about the Ping of Death, read my huge response to this very thread, here! (I have copied his response to the end of the tutorial)
Step 1
Make a page that lets you submit forms. Method='GET' is better than method='POST' for this, but both will work.
(If you do not understand step 1, just find a page that lets you submit information, like a new comment or upload a picture)
Step 2
Fill out the forms and submit
Step 3
Reload the page
If the page uses the POST method your browser will display a dialog asking if you are sure you want to resend the information, or something to that effect. Simply click "Continue" or "OK".(see now why GET is better?)
Step 4
Keep reloading until server is down.
Their are many add ons and tools that allow you to auto-reload a page. It is a matter of googleing for them. They are widely available and free.
I have just created a program that allows you to Auto-refresh a page using IE. If you are interested please download from:
Host: Darksunlight.com | Size: 9kb | Format: .zip ultra compressed | Platform: Windows
Use the browser extensions instead. Google for auto reload addons for your browser.
This method is very primitive as you can see, but it is probably the best way to DDoS.
In order to learn more about DDoS by reload, read my huge response to this very thread, here!
(I have copied his response to the end of the post)
(He has stressed the fact enough, but let me remind you again, this is a punishable offense. Use LOIC only on your localhost 127.0.0.1. Don't use it on any online server, they cops will come to get you. In contrast to all other tools on this blog, this one works on Windows.)
Download:
LOIC | Host: SourceForge
Step 1
Download and extract LOIC
Step 2
Open LOIC.exe and fill out the required information.
Instructions for filling out:
IP or URL = IP or URL that you wish to DoS
TCP / UDP message = information being sent, just write something random. Or leave it as default.
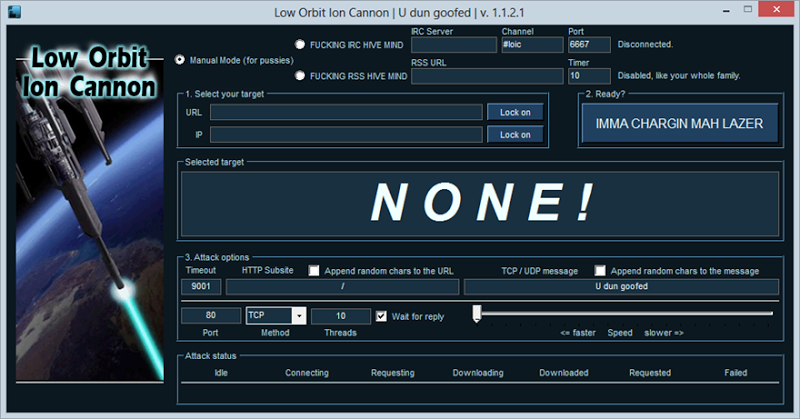 Port = Server's port
Port = Server's port
Method = Server's Method, leave as TCP if unknown
If you are gonna try to take down a website then use HTTP
Speed = set to "<= faster"
Threads = How many users it should simulate, the higher the number the faster it will crash. Set to 10,000. Note that this might make your computer lag, if so, set to a lower amount.
Step 3
Click on "IMMA CHARGIN MAH LAZER"
This starts your the program.
Warning: This tool might not seem like much, but many people of all ages have been arrested and convicted for knowingly using this tool. Remember DoS and DDoS are federal crimes, however insignificant it may seem. Use at your own discretion.
Their are still many other ways to attack a server, but these are the basics of DoS.
Protect your servers xD
Like any web developer I hope you will use this information for the good.
Sadly i know that their are those among us that are, even now as we read this, plotting how to do harm with this information.
To those, I flip the bird.
What is "DDoS"?
Denial of Service attacks(or Distributed Denial of Service attacks[DDoS]) are a form of organized attacks with the goal of taking down a server by overloading it. Often by sending useless information(packets) to a server in massive amounts.
In-fact about a year ago I found one of my (his) websites was accidentally DoS-ing darksunlight.com(I use darksunlight as my webhost) because my PHP script made an infinite loop that sent the same information over and over and over into darksunlight's SQL databases. This one page took this EXTREMELY powerful server down twice in less than a minute. That site has since been deleted.
That story demonstrates that it does not take more than a simple "error" in your code to overload a server.
Keep in mind that altough spreading knowledge is my main goal, performing DDoS attacks is indeed a federal crime in the US.
It is also an international offence and will be punished according to the local laws of the individual's country.
But enough talk. I will now show you a quick example of a DoS attack of sorts you can do on your local computer.
Example Of DOS attack
Keep in mind that this is NOT a real DoS attack, but rather an example to visualize how a DoS attack works.We will take down YOUR computer.
Step 1
Open up notepad, mousepad, or your favored equivalent.
Step 2
Type in this simple batch command
Code:
:a
start
goto a
Step 3
Save as "dossample.bat" making sure you select "All files" from the "File Type" dialog.
Step 4
Run that sucker, but save your work first, as this will crash even the best computers in a matter of minutes.
What did you learn from this?
Observe how the file rapidly replicates itself, opening a new CMD right after it opens another.An infinite loop has been created that has filled the RAM with useless and massive amounts of CMDs(or Terminals for you Unix folk)
DDoS attacks work much the same way, except instead of replicating an infinite number of CMDs, they send information(packets) to the server over and over and over again until the server crashes.
What information you may ask?
Anything. Your login name, your 'online' status, a new comment, the number of views on a video, your new high score. Absolutely any information that could be resent a massive amount of times to the same server.Next we will be discussing the simplest form of DDoS.
DDoS by Ping Flood
Please note that I will be pinging my Localhost. You should too.
Perhaps one of the simplest ways to DoS is by using the 'ping' command built into most operating systems, including all windows and Linux distributions.
Step 1
Start up your server. Mine is apache, but that is beside the point, the server type does not matter. If it has an IP address, it can be pinged. (He paced up really unexpectedly here. You might want to skip this part if you haven't created any local server using apache or any other program.)
Step 2
Type in the ping command
Code:
ping -t -a -l 65500 localhost
Step 3
Press enter and watch it ping the localhost over and over until[/b]
your server crashes, or you get tired of waiting for it to crash.
Since most modern servers can take the stress of the ping flood, you will need to get all your friends to help you ping to bring your server down. Or even slow it down.
Command Explained
ping - tells the computer to ping a server-t - It will continue to ping the server until the command is closed, or stopped.
-a - Resolves the adress to host names.
-l - Size.
By default the ping will send 32bytes of data to the server, so you must change this to a bigger number. The maximum is 65,500bytes, so that is what we used.
If you send a server any number higher than 65,500bytes it will instantly crash. This is called "Ping of Death".
Like any other thing with the suffix "of Death" it is very rare, and hard to accomplish indeed.
In order to learn more about the Ping of Death, read my huge response to this very thread, here! (I have copied his response to the end of the tutorial)
DDoS by Reloading
Something as simple as reloading a page can take down a server if done enough times.Step 1
Make a page that lets you submit forms. Method='GET' is better than method='POST' for this, but both will work.
(If you do not understand step 1, just find a page that lets you submit information, like a new comment or upload a picture)
Step 2
Fill out the forms and submit
Step 3
Reload the page
If the page uses the POST method your browser will display a dialog asking if you are sure you want to resend the information, or something to that effect. Simply click "Continue" or "OK".(see now why GET is better?)
Step 4
Keep reloading until server is down.
Their are many add ons and tools that allow you to auto-reload a page. It is a matter of googleing for them. They are widely available and free.
Use the browser extensions instead. Google for auto reload addons for your browser.
This method is very primitive as you can see, but it is probably the best way to DDoS.
In order to learn more about DDoS by reload, read my huge response to this very thread, here!
(I have copied his response to the end of the post)
Low-Orbit Ion Cannon
LOIC (Low Orbit Ion Cannon) is an app, written in C# and developed by praetox, that was used by Anonymous during Project Chanology. It attempts to DoS the target site by using all its bandwidth, sending TCP, UDP, or HTTP requests to the server until it crashes.(He has stressed the fact enough, but let me remind you again, this is a punishable offense. Use LOIC only on your localhost 127.0.0.1. Don't use it on any online server, they cops will come to get you. In contrast to all other tools on this blog, this one works on Windows.)
Download:
LOIC | Host: SourceForge
Step 1
Download and extract LOIC
Step 2
Open LOIC.exe and fill out the required information.
Instructions for filling out:
IP or URL = IP or URL that you wish to DoS
TCP / UDP message = information being sent, just write something random. Or leave it as default.
 Port = Server's port
Port = Server's portMethod = Server's Method, leave as TCP if unknown
If you are gonna try to take down a website then use HTTP
Speed = set to "<= faster"
Threads = How many users it should simulate, the higher the number the faster it will crash. Set to 10,000. Note that this might make your computer lag, if so, set to a lower amount.
Step 3
Click on "IMMA CHARGIN MAH LAZER"
This starts your the program.
Warning: This tool might not seem like much, but many people of all ages have been arrested and convicted for knowingly using this tool. Remember DoS and DDoS are federal crimes, however insignificant it may seem. Use at your own discretion.
Conclusion
Now you know what a DDoS attack is and you can work to better protect your self.Their are still many other ways to attack a server, but these are the basics of DoS.
Protect your servers xD
Like any web developer I hope you will use this information for the good.
Sadly i know that their are those among us that are, even now as we read this, plotting how to do harm with this information.
To those, I flip the bird.
Response to Reloading method and ping of death
Question :
This is a really good theoretical tutorial. Some questions I have though are number 1, how do you make the ping send a packet larger than 65000? And isn't that a really old exploit that only works <=win95?
I also really have doubts about the reloading method. Is it just a theoretical thing that if a site is small enough it could work, or is there actually a practical possibility of it? Are there any examples?
Response:
Both very good questions.
1. The ping of death, or a packet larger than 65,000 is, in fact, a really old exploit that most servers and operating systems have patched. But not all.
It is still quite possible for the Ping of death to work, often with mixed results.
Some of the vulnerable operating systems are:
Solaris(x86 version) 2.5 & 2.5.1a
MkLinux
Windows NT(mixed results, after microsoft released patch)
Linux, below version 2.0.23
Windows 95
Novell Netware 3.X.X
MacOS <= 7.X.X
And many others...
For a full list of vulnerable operating systems, and their response to a ping of death attack, visit this page.
2. The reloading method is not only practically plausible, but it happens every day, and most often in accident.
Let me explain, go to... let's say, the front page of hackforums, and hit CTRL+S, this will save the webpage into your hard drive. It will most likely be located under your downloads folder, check the properties for that web document, and all attached files.
The size of the front page of hackforums.net, including all elements displayed(images, CSS files, separate JS file, ect...) is around 500KB.
This might not seem like much, that's much less than the average size of a picture taken with any recent digital camera, but consider this:
As I type this, there are currently around 729 members actively surfing the website. Each of them is downloading around 500KB of data from this server, simple arithmetic tells us that's a total of 364,500KB(roughly 356MB of data, or about the size of a standard definition feature length video-film) of data.
356MB of data that was transfered from the hackforums.net server, into 729 separate connections.
Still doesn't sound like a lot, does it?
Hackforums.net gets an average of 5 page views, per visitor. That means that each of those 729 people that are online right now, will visit around 5 pages before they leave the site.
Supposing that every page in hackforums.net has a similar size to the front page, of ~500KB(in fact most pages are somewhat larger than that), and knowing that there is a total of 729 people currently online, and supposing that each of them will visit an averge of ~5 pages, then we can create a simple formula to calculate the server stress at this point in time.
X = Average size of a page(~>=500kb)
Y = Visitors online(~729 ATM)
Z = Average of ~5 pages viewed, per visitor
D = Data transfer at any given point
D = (X*Y)*Z
This gives us a total of 1,822,500KB or about 1.73GB(roughly the size of an HD 720p feature length video-film).
That's 1.73GB of data that has just been transferred from hackforums.net to 729 separate connections.
Still doesn't sound like a lot, right? Well, this has been the total transfer for the past ~5 minutes or so.
In reality hackforums employs many techniques to minimize data transfers, and so does your browser. Things like an indexed cache or offline stored data can minimize the number of things that have to be downloaded from the web server every time you load(or re-load) a page.
I calculated a total daily download transfer of around 1,133GB per day(roughly 285 FullHD 1080p feature length video-films) for hackforums.net, but you can be sure that it's much larger than that.
Even then we're only accounting for data transferred as downloads.
We're not even touching the immense amount of uploads, connection request, resolves, pings, local data transfers, SQL INSERTs/UPDATEs/DELETEs, and a slew of other processes that occur every time you load a page.
Let me give you a quick example, in case my explanation wasn't enough.
On October, 25th, 2011 the popular web adventure/comic "Homestuck" released the final page of their 5th 'act' or volume.
The last page was released in the form of a, VERY LONG and VERY AWESOME, flash animation that was around 250KB in size.
(You are welcome to experience it here.)
Said flash animation was hosted on the capacious flash portal, newgrounds.com
Keep in mind that newgrounds.com is a website that experiences millions of daily visits, and they serve flash files that range from a couple KBs to >~100MBs without even breaking a sweat.
Within less than an hour of the release, both newgrounds.com AND the homepage of the homestuck webcomic had been taken down by their own fanbase.
Everyone was so exited to finally see the last page, that they all rushed in to see the animation at once, and thus crashed both websites with ease.
Both websites kept crashing multiple times during the day, until all the fans had seen it, and had thus stopped loading and reloading that page.
So to recap, not only is DoS by page reload plausible, but it is, without a doubt, the most effective method of DDoS.
_________________________________________________
So this is all there was to the tutorial. I hoped you liked it. If you have any queries feel free to ask.













