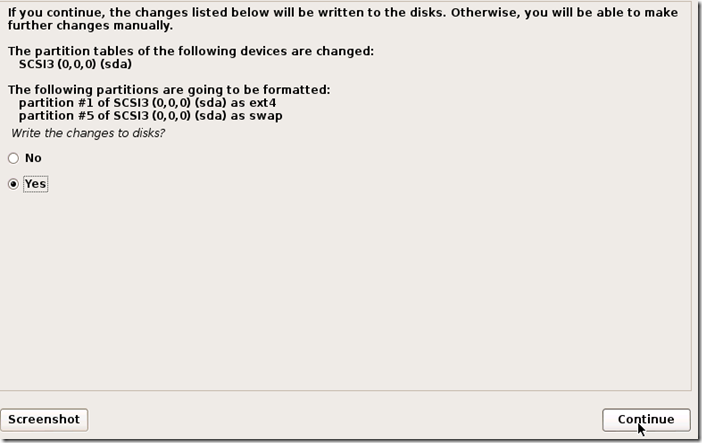
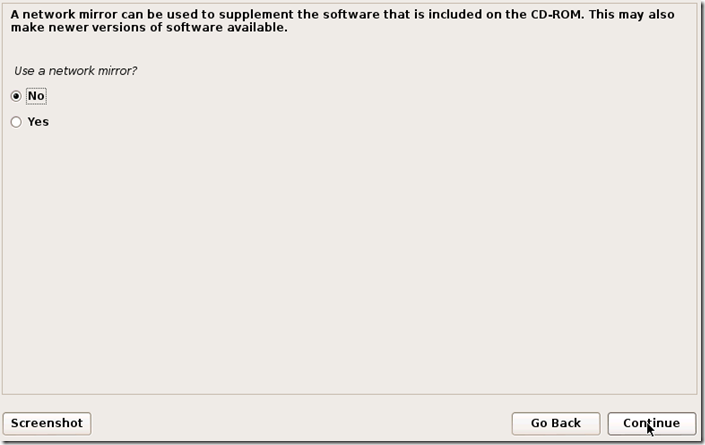
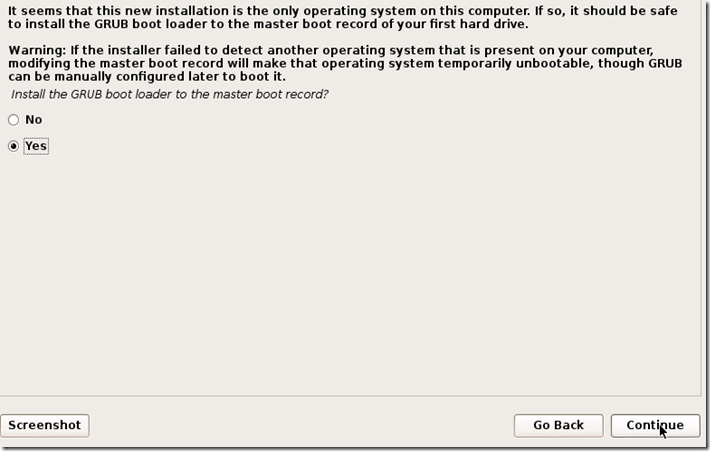
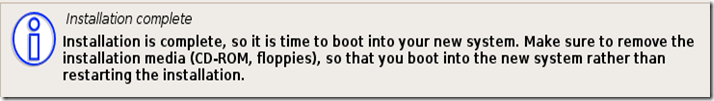
Ah! The world of hackers. It has changed much from the fabled green black terminal operated by guys with spectacles on their eyes and a serious look on their face. Now even a script kiddie who types a few lines on a Kali Linux calls himself a hacker. The terminal is still there, but the colors have changed. It's black terminal with text of all colors. But who cares about the colors. It's the new Operating Systems : The likes of Kali Linux,
Ah! The world of hackers. It has changed much from the fabled green black terminal operated by guys with spectacles on their eyes and a serious look on their face. Now even a script kiddie who types a few lines on a Kali Linux calls himself a hacker. The terminal is still there, but the colors have changed. It's black terminal with text of all colors. But who cares about the colors. It's the new Operating Systems : The likes of Kali Linux,Backtrack, BackBox Linux, Node Zero, Blackbuntu, and many more, which have made hacking much easier. However, has it got easy enough? No. Not at all.
It's getting harder
When the going gets tough, the tough get goingWhile Kali Linux can make hacking Windows XP, wirless networks, and some weak websites very easy, it doesn't mean it is a magical solution to all problems. Everything that can be hacked easily is ancient. No one uses Windows XP anymore, and if they do, the machines are patched because of automatic updates. Very few websites are vulnerable to the standard SQL injection attacks. You'll have to think up and use variants of standard injections to counter the defenses. Yes, WEP networks are easy to hack, and are still abundant, especially in developing countries. But if you want to hack Facebook, then you should step back already, you're going the wrong direction. Facebook isn't paying millions for security so that a kid can Google up the procedure to hack FB and be done with it overnight. But wait, how could I even imagine that you've already reached this point. While all this hacking XP and WEP shit is pretty easy, is it okay to assume you can do it, and are worried about the 'harder' part. Or wait, are you experiencing difficulty in even using Kali Linux. Can't figure out how to install it. Well...
Oh well
First time is always the hardestIn the previous few paragraphs I made a big mistake. I assumed that you have installed Kali Linux and can do some basic stuff with it, and the intermediate level tasks are bothering you. I almost forgot how it was for me. Well let me tell you.
- I was 12. Wanted to hack this wireless network next door.
- Download some shitty Windows software. Won't work. Plus had malware installed which had to be removed with antivirus.
- More googling, came across BT4. Googled up some tutorials on how to install it. Was too stupid for Vmware. Live? No. Couldn't create a bootable USB. I downloaded the OS and simply copied it to the USB and thought it'll boot. Googled more. Some result said something about boot order. Okay, make USB boot before hard disk. Made some sense, but it wouldn't work. As it is, I was scared as hell when modifying stuff in the scary looking BIOS interface. Hoping I don't do any damage.
- Some time later, BT5 was released. Me? A bit smarter this time. Could get BT5 to boot. Read some WEP hacking tutorials. Wasn't able to follow. I even had a tough time with getting the GUI to start. In BT5 we had to type startx for starting X Display server. Didn't know that. Finally, hacked wifi using Aircrack-ng GTK or something (don't remember the name exactly, but it was GUI mode of aircrack, and it was pretty easy for a beginner like me to use it).
- Took me an year before I knew how to do stuff without GUI. An year sounds like a long time, but remember, I have much more stuff to do than just hack. I used BT5 once every few months, only when a new network would show up in the neighbourhood, and I would hack it with my laptop.
- Had a great sense of accomplishment inside me. Felt like I was king of this territory, and owned every wireless network here. But then, a WPA-2 network appeared. I tried everything I could, but gave up. I read on hackforums a tutorial on using WPS vulnerability to hack WPA. Well, it looked like it was written in an alien language. Honestly, after knowing how easy hacking WPS enable WPA networks is, I seriously think that the first time indeed is the hardest.
- Fast forward to this moment. I have mastered the basics of linux command line interface, but still have a lot to learn. I can write bash scripts to automate stuff, and can use most of the tools with ease. I am currently studying exploit development and research and can write simple exploits. There's a lot left to learn. I know the depths of wireless pentesting, but only intermediate level of web pentesting. I know the basics of social engineering, but again, lot of things to learn. Now if you are concluding I'm an idiot on the basis of the fact that in every field I just know the basics, well then you need to realize that the meaning of basics in my perspective is much different from that in yours. I need to know a lot of stuff, but I know a lot too.
So what do you conclude from this? Well if you are not able to install Kali, or follow any other tutorial in my website, then don't be surprised. If everyone who visits this website became a hacker, then we'd be having more than 100k hackers created from this website alone, which isn't a good thing at all, considering there are many other websites which receive much more traffic than mine.
Why so difficult
Hacking is an art
Because that's the way it is. Hacking is an art, and like any other, it takes practice, hard work and determination to master this art. For example, after watching dynamo on TV, I got lured into the idea of becoming a magician. Well, I tried some tricks, but failed miserably. Realized it was not my piece of cake. Some of the tricks require years of practice before they can be pulled off successfully. Not everyone who decides to be a magician ends up becoming one. There are obstacles in the way, disappointments, milestones too hard too achieve. The ones who stay determined all the way to the end only achieve this. It's not everyone's piece of cake. Same goes with hacking. What makes hackers exclusive and special is the fact that not everyone is a hacker. I am known in my class (whole school as well) for being a hacker. Why? Because I'm the only one. Not everyone who sets out to be a hacker becomes one. But there's more to the story than this.
Not that difficult
You are lucky that you ended up on this blog (not a quote as such)
 Well, the sites I used to learn hacking were crap. The WEP tutorial was just 3-4 lines of code and no
Well, the sites I used to learn hacking were crap. The WEP tutorial was just 3-4 lines of code and no explanation. I won't be wrong if I say that, while I read a lot of tutorials, none was good enough. For every line in a tutorial, I had to google up another tutorial which explained what it meant. That is, I worked hard and figured everything out on my own. You, however, are lucky. The posts in this blog have been written such that everything is properly explained. In the later tutorials I have been a bit lazy, but it won't be a problem if you follow the tutorials in correct sequence. If you have read 2-3 tutorials on pentesting, you would already know the basics, and the 4th one wouldn't have to be very detailed. If you jump to Win 7 hacking without going through XP, then you'll encounter difficulties. Now I have created a page on this blog where I have ordered the posts in the desirable order of reading. You might also look at the navigation menu on top and read all the tutorials on a top to bottom order basis. And here's the truth finally.
The truth
I want to hack facebookIf you are learning hacking to hack your friends account, then you're never going to become a hacker. Just hire someone to do it. Because the time and effort you'll invest in making an attempt to learn how to do it yourself, and eventually failing in the same, is much more valuable than the money required to hire someone (no I don't hack FB accounts for money). You might still try social engineering, but it is not a 100% working method, and well, phishing is not hacking, and is illegal. However, if you're motives aren't that selfish, and if you are on a quest for knowledge, then rest assured, you will achieve success. Also , you need to know the art of google-fu. If you face any difficulties, remember, google is a friend (and so am I, I have replied to 100s of comments on this blog personally and always get people through difficulties). The last thing, 50% of the people who come to this blog leave within 1 min of their visit, after seeing just one page. 30% stay for 4-10 mins and read 2 posts. 20% stay for more than 10 minutes, and keep coming back. Only these 20% successfully will become a hacker. Either they succeeded in achieving what they wanted, loved the blog, and came back for more, or they didn't succeed, but came back to try again, and I'm sure they would succeed on a second attempt. Remember, never give up. Less than 20% of the visitors here actually succeed in getting what they want, try and be in that 20%. And if you have any suggestion for this post or for my way of explanation or anything else in general, please comment.